Conference
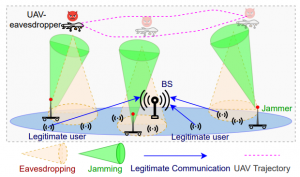
Ear in the Sky: Terrestrial Mobile Jamming to Prevent Aerial Eavesdropping
Conference
The 2021 IEEE Global Communications Conference (GLOBECOM), 2021, Madrid, Spain (On-site & Virtual)
Publication year: 2021
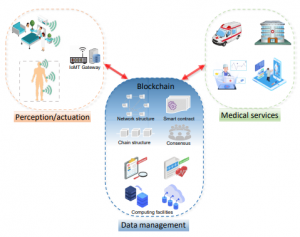
Coverage Analysis of Blockchain-enabled Wireless IoMT Networks
Conference
2021 IEEE Globecom Workshops (GC Wkshps): Workshop on Scalable, Secure and Intelligent Blockchain for Future Networking and Communications
Publication year: 2021
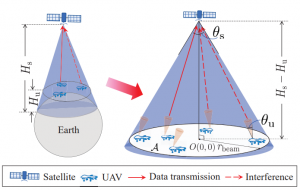
Connectivity Analysis of UAV-To-Satellite Communications in Non-Terrestrial Networks
Conference
The 2021 IEEE Global Communications Conference (GLOBECOM), 2021, Madrid, Spain (On-site & Virtual)
Publication year: 2021
Complex Network Analysis of the Bitcoin Blockchain Network
Conference
IEEE International Symposium on Circuits & Systems (ISCAS), Daegu, Korea, 2021 (On-site \& Virtual)
Publication year: 2021
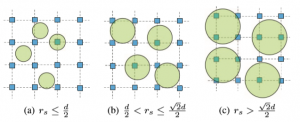
On UAV-assisted Data Acquisition for Underwater IoT in Aquaculture Surveillance
Conference
Proceedings of 5th International Conference on Maritime Technology and Engineering (MARTECH 2020)
Publication year: 2020
LSH-based Collaborative Recommendation Method with Privacy-Preservation
Conference
IEEE International Conference on Cloud Computing (IEEE CLOUD), 2020
Publication year: 2020
Fused 3-Stage Image Segmentation for Pleural Effusion Cell Clusters
Conference
Proceedings of the 25th International Conference on Pattern Recognition (ICPR), 2020
Publication year: 2020
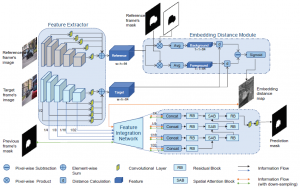
Distance-Guided Mask Propagation Model for Efficient Video Object Segmentation
Conference
Proceedings of the 2020 International Joint Conference on Neural Networks (IJCNN 2020)
Publication year: 2020
Cryptocurrencies Price Prediction Using- Weighted Memory Multi-Channels
Conference
The 2020 International Conference on Blockchain and Trustworthy Systems, 2020
Publication year: 2020
Boosting UI Rendering in Android Applications
Conference
Proceedings of 2020 IEEE 20th International Conference on Software Quality, Reliability and Security Companion (QRS-C)
Publication year: 2020
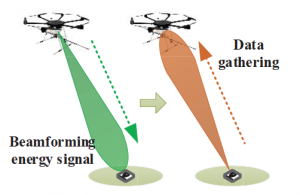
UAV-enabled Data Acquisition Scheme with Directional Wireless Energy Transfer
Conference
International Conference on Embedded Wireless Systems and Networks (EWSN) (Poster session)
Publication year: 2019
Portable Convolution Neural Networks for Traffic Sign Recognition in Intelligent Transportation Systems
Conference
IEEE International Conference on Cyber Physical and Social Computing (CPSCom), 2019
Publication year: 2019
MHDT: A Deep-Learning-based Text Detection Algorithm for Unstructured Data in Banking
Conference
11th International Conference on Machine Learning and Computing, 2019
Publication year: 2019
Gold Price Forecast based on LSTM-CNN Model
Conference
The 5th International Conference on Cloud and Big Data Computing (CBDCom), 2019
Publication year: 2019
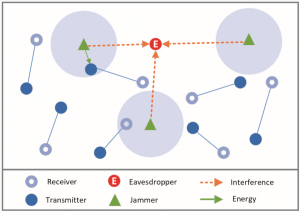
When Friendly Jamming Meets Wireless Energy Transfer
Conference
IEEE International Conference on Green Computing and Communications 2018, Halifax, Canada
Publication year: 2018