Journal
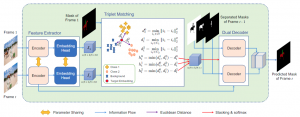
TMVOS: Triplet Matching for Efficient Video Object Segmentation
Journal
Signal Processing: Image Communication, Volume 107, September 2022, 116779
Publication year: 2022
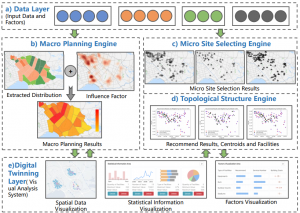
SpoVis: Decision Support System for Site Selection of Sports Facilities in Digital Twinning Cities
Journal
IEEE Transactions on Industrial Informatics, vol. 18, no. 2, pp. 1424-1434, Feb. 2022
Publication year: 2022
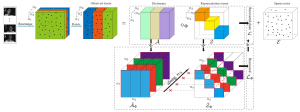
Robust Corrupted Data Recovery and Clustering via Generalized Transformed Tensor Low-rank Representation
Journal
IEEE Transactions on Neural Networks and Learning Systems, 2022, doi: 10.1109/TNNLS.2022.3215983.
Publication year: 2022
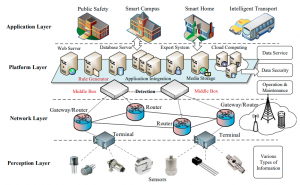
Privacy-Preserving Encrypted Traffic Inspection with Symmetric Cryptographic Techniques in IoT
Journal
IEEE Internet of Things Journal (early access), doi: 10.1109/JIOT.2022.3155355
Publication year: 2022
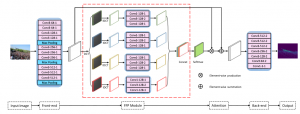
Frequency Feature Pyramid Network with Global-Local Consistency Loss for Crowd and Vehicle Counting in Congested Scenes
Journal
IEEE Transactions on Intelligent Transportation Systems, 2022, doi: 10.1109/TITS.2022.3178848
Publication year: 2022
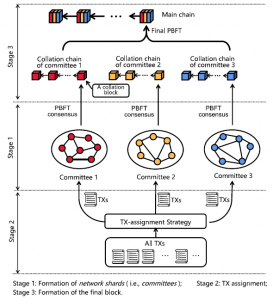
Elastic Resource Allocation against Imbalanced Transaction Assignments in Sharding-based Permissioned Blockchains
Journal
IEEE Transactions on Parallel and Distributed Systems, vol. 33, no. 10, pp. 2372-2385, 1 Oct. 2022, doi: 10.1109/TPDS.2022.3141737
Publication year: 2022
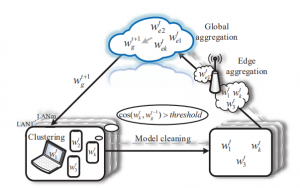
Edge-Based Communication Optimization for Distributed Federated Learning
Journal
IEEE Transactions on Network Science and Engineering, (early access) 2021
Publication year: 2022